“Unmasking Deception: Was This Starlet a Honey Pot or a Chinese Spy?”
Chinese espionage tactics, honey trap victim stories, intelligence agency infiltration
—————–
Understanding the Dynamics of Espionage and Honey-Trapping in Modern Contexts
In the contemporary world of espionage, the lines between intelligence gathering and personal relationships can often blur. A recent tweet by actor and commentator James Woods highlights a striking visual narrative involving two individuals: one identified as a Chinese spy and the other as a honey-pot trap victim. This image and its accompanying commentary bring to light the complex interplay between espionage tactics and personal vulnerabilities, underscoring the need for heightened awareness in an increasingly interconnected world.
What is Honey-Trapping?
Honey-trapping is a sophisticated espionage technique where an agent entices a target into a romantic or sexual relationship to extract sensitive information. This tactic exploits emotional and psychological vulnerabilities, making it a powerful tool in the arsenal of spies. The honey-pot trap can lead to compromised individuals revealing classified information, thereby posing significant risks to national security.
The Role of Chinese Espionage
China has been frequently highlighted in discussions surrounding espionage due to its extensive intelligence operations worldwide. The Chinese government has been accused of employing various methods to gather sensitive information, ranging from cyber espionage to traditional human intelligence (HUMINT) operations. The mention of a "Chinese spy" in Woods’ tweet suggests the ongoing relevance of Chinese espionage tactics in global affairs.
- YOU MAY ALSO LIKE TO WATCH THIS TRENDING STORY ON YOUTUBE. Waverly Hills Hospital's Horror Story: The Most Haunted Room 502
Chinese spies are known to infiltrate various sectors of society, including politics, military, and technology. Their operations often involve cultivating relationships within influential circles, where they can access confidential information. This approach not only highlights the significance of traditional spy craft but also emphasizes the evolving nature of intelligence gathering in the digital age.
The Vulnerability of Individuals
The concept of vulnerability is central to understanding the effectiveness of honey-trapping. Individuals in positions of power or influence may become targets due to their access to sensitive information. Factors contributing to their vulnerability can include personal circumstances, emotional loneliness, or the desire for validation. This emotional manipulation is often what makes honey-trapping so effective.
In the case depicted in Woods’ tweet, the honey-pot trap victim may have been someone who, for various reasons, was open to forming a relationship with a stranger. This dynamic is not just limited to romantic pursuits; it can also extend to friendships and professional relationships. The emotional investment in these connections can cloud judgment, leading to unguarded moments where sensitive information is disclosed.
The Implications of Espionage
The implications of espionage and honey-trapping extend beyond individual victims. Each successful honey-pot operation can have far-reaching consequences for national security, corporate integrity, and international relations. When sensitive information is leaked, it can undermine trust, provoke diplomatic tensions, and even lead to conflicts.
Furthermore, as technology evolves, the methods employed by spies also adapt. Cyber tools and social media platforms have changed the landscape of espionage, allowing spies to gather intelligence more discreetly. This evolution necessitates a continuous reassessment of security protocols and personal awareness among individuals who may be at risk.
Recognizing the Signs
For individuals who may find themselves in vulnerable positions, recognizing the signs of a honey-trap is crucial. Some common indicators include:
- Overly Personal Questions: If someone is probing into your personal life too quickly, it may be a red flag.
- Unusual Generosity: Be wary of individuals who shower you with gifts or attention without a clear reason.
- Pressure to Share Information: If someone is pushing you to disclose sensitive information, trust your instincts and proceed with caution.
- Inconsistencies in Their Story: Pay attention to any discrepancies in what someone tells you about themselves.
Building Awareness and Resilience
To combat the threat of espionage and honey-trapping, individuals and organizations must prioritize awareness and resilience. Education about the tactics used by spies can empower individuals to protect themselves from manipulation. Additionally, fostering a culture of transparency and communication within organizations can help mitigate risks.
Organizations should implement comprehensive training programs that educate employees about the potential dangers of social engineering and espionage tactics. Developing a robust security culture can encourage individuals to report suspicious behavior without fear of reprisal.
Conclusion
The interplay of espionage and personal relationships, as illustrated in James Woods’ tweet, serves as a cautionary tale in our increasingly interconnected world. The tactics employed by spies, such as honey-trapping, emphasize the importance of understanding vulnerability and the potential implications of compromised information. By recognizing the signs and fostering awareness, individuals and organizations can take proactive steps to protect themselves from the intricate web of espionage that may lurk within personal and professional relationships.
As we navigate the complexities of modern life, it is essential to remain vigilant and informed about the tactics employed by those who may seek to exploit emotional vulnerabilities for their gain. In doing so, we can safeguard our personal and organizational integrity against the ever-evolving landscape of espionage.

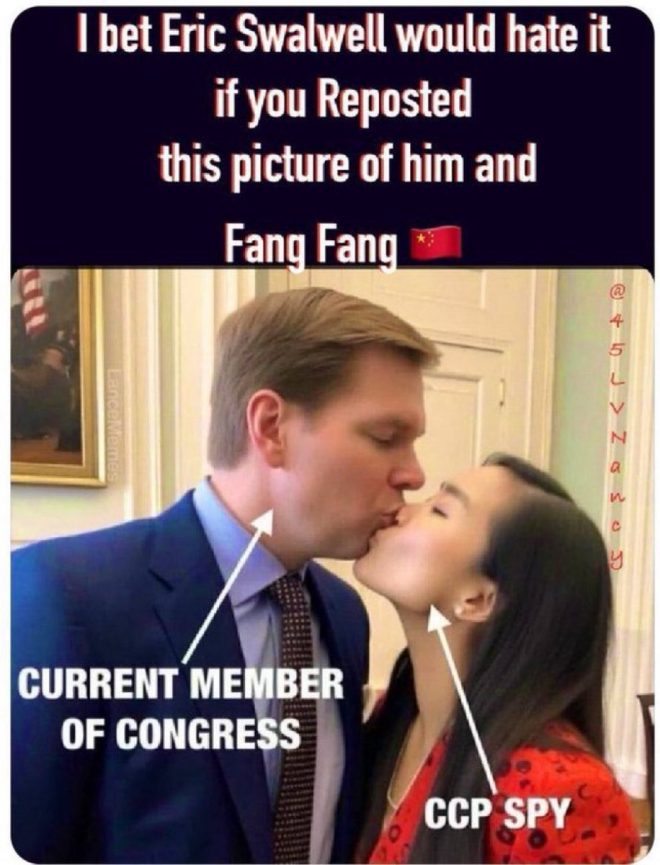
One of these people was a Chinese spy. The other is a honey-pot trap victim. pic.twitter.com/KZ7l2JhCXz
— James Woods (@RealJamesWoods) June 9, 2025
One of these people was a Chinese spy. The other is a honey-pot trap victim. pic.twitter.com/KZ7l2JhCXz
— James Woods (@RealJamesWoods) June 9, 2025
One of these people was a Chinese spy. The other is a honey-pot trap victim.
When scrolling through social media, you might come across intriguing posts that spark curiosity and provoke thought. One such tweet by actor James Woods captured the attention of many, featuring a striking image with the caption, “One of these people was a Chinese spy. The other is a honey-pot trap victim.” This simple yet enigmatic statement opens a can of worms about espionage, deception, and the lengths to which some individuals go to gather information.
In this article, we’ll delve into the world of espionage, the concept of honey-pot traps, and the implications of such tactics in modern times.
Understanding Espionage
Espionage is the act of spying or using spies to gather secret information, primarily for military or political purposes. Countries have engaged in espionage for centuries, employing various methods to obtain intelligence. In recent years, the focus has shifted towards cyber-espionage and the use of technology to infiltrate systems and extract sensitive data.
The mention of a “Chinese spy” in Woods’ tweet isn’t just sensationalism. Reports suggest that China has been involved in numerous espionage activities globally, targeting everything from technological innovations to military secrets. For example, the FBI has raised concerns about China’s alleged efforts to steal U.S. technology and trade secrets, leading to a heightened awareness of the need for security measures in both the public and private sectors.
The Role of Honey-Pot Traps
Now, let’s dive into the idea of a honey-pot trap. This term refers to a tactic used to lure individuals into compromising situations, often involving seduction or manipulation. The term evokes images of traps laid out with enticing bait, leading unsuspecting victims into dangerous waters.
In the context of espionage, honey-pot traps are often employed to gain information or leverage over an individual. For instance, a spy might use charm and allure to develop a relationship with a target, ultimately leading them to divulge sensitive information. This method can be incredibly effective, as it preys on human emotions and vulnerabilities.
A notable example of a honey-pot trap involves the case of Anna Chapman, a Russian spy who was arrested in the U.S. in 2010. She used her looks and charm to infiltrate social circles and gain access to important individuals, showcasing the effectiveness of this tactic in the realm of espionage.
The Impact of Honey-Pot Tactics on National Security
The implications of honey-pot traps are vast and far-reaching. For governments and organizations, the threat of espionage remains ever-present, and the use of honey-pot tactics only complicates the landscape. As individuals become more interconnected through social media and other platforms, the risk of falling into such traps increases.
It’s essential for individuals in sensitive positions to remain vigilant. Familiarizing oneself with the tactics employed by spies can be a crucial step in safeguarding personal and organizational information. Many organizations are now implementing training programs to help employees recognize potential honey-pot traps and other espionage tactics.
Real-Life Cases of Espionage and Honey-Pot Scenarios
Real-life instances abound where individuals have fallen prey to honey-pot traps. One of the most infamous cases involves the Cold war, where spies from both the East and the West utilized seduction and charm to gather intelligence. These historical instances serve as a testament to the effectiveness of honey-pot tactics.
In the digital age, the stakes have grown even higher. With the rise of social media, it has become increasingly easy for spies to create fake personas and engage with individuals online. This tactic allows them to build trust and rapport, paving the way for sensitive information to be shared.
Take, for instance, the case of several Russian operatives who posed as Americans on social media platforms like Facebook and Twitter, forming relationships with unsuspecting individuals to gain insights into U.S. politics and society. This highlights how honey-pot traps are evolving with technology, making it essential for individuals to be cautious about what they share online.
Protecting Yourself from Honey-Pot Traps
So, how can you protect yourself from falling victim to honey-pot traps? Here are a few key strategies to consider:
1. **Be Cautious with Personal Information**: Always think twice before sharing personal details, especially on social media. Spies often look for information that can be used against you or to gain leverage.
2. **Verify Relationships**: If someone seems too good to be true, they just might be. Take the time to verify the identities of individuals you interact with, especially if they are asking for sensitive information.
3. **Educate Yourself and Others**: Awareness is your best defense. Educate yourself and encourage your peers to recognize potential honey-pot traps and other espionage tactics.
4. **Report Suspicious Activity**: If you encounter someone who raises red flags, don’t hesitate to report your concerns. It’s better to be safe than sorry.
Conclusion
The interplay between espionage and honey-pot traps remains a fascinating yet concerning topic. James Woods’ tweet highlighting the contrast between a Chinese spy and a honey-pot trap victim serves as a reminder of the complexities of modern intelligence gathering.
As technology continues to evolve, so too do the tactics employed by those seeking to exploit vulnerabilities. By staying informed and vigilant, individuals can better protect themselves against the ever-present threat of espionage and manipulation. The world of intelligence may be shrouded in secrecy, but understanding its mechanisms can empower you to navigate it safely.
As always, remain cautious and informed—your safety and security depend on it.
